Navigating the Network: A Comprehensive Guide to Network Security Assessments (NSA) Maps
Related Articles: Navigating the Network: A Comprehensive Guide to Network Security Assessments (NSA) Maps
Introduction
With great pleasure, we will explore the intriguing topic related to Navigating the Network: A Comprehensive Guide to Network Security Assessments (NSA) Maps. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Network: A Comprehensive Guide to Network Security Assessments (NSA) Maps
![What is a Network Security Assessment? [+How to Conduct & Best Tools]](https://gogetsecure.com/wp-content/uploads/2022/03/What-Tools-Are-Used-in-Network-Security-Assessment.jpg)
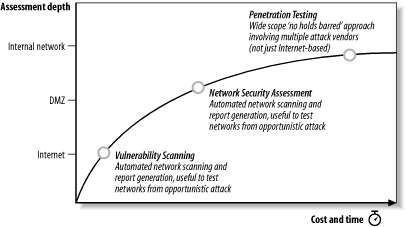
In the contemporary digital landscape, safeguarding networks from cyber threats is paramount. This necessitates a proactive approach, involving comprehensive security assessments that identify vulnerabilities and guide mitigation strategies. One such assessment, known as a Network Security Assessment (NSA) map, provides a detailed blueprint of an organization’s network infrastructure, revealing potential security weaknesses and highlighting areas requiring immediate attention.
Understanding the Essence of NSA Maps
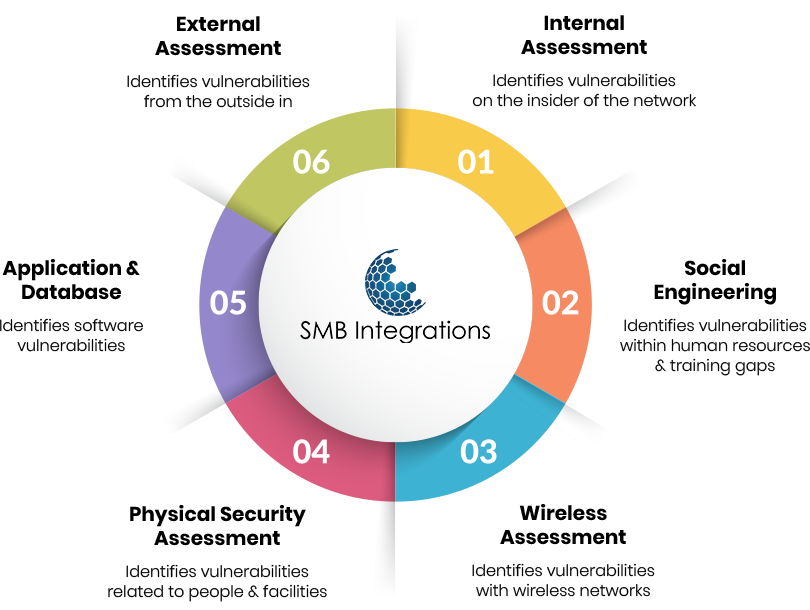
An NSA map serves as a visual representation of an organization’s network infrastructure, encompassing all connected devices, systems, and applications. This map goes beyond a simple diagram, incorporating crucial security information about each element, including:
- Device Type: Identifying each device, whether a server, workstation, router, firewall, or other network component.
- Operating System: Specifying the operating system running on each device, revealing potential vulnerabilities based on known security flaws.
- Software Applications: Listing all installed software applications, including their versions, to identify potential vulnerabilities and outdated software requiring updates.
- Network Connectivity: Illustrating the connections between devices, including wired and wireless connections, to understand potential attack vectors.
- Security Measures: Detailing implemented security measures, such as firewalls, intrusion detection systems (IDS), and antivirus software, to assess their effectiveness and identify gaps.
- User Access: Mapping user accounts and their privileges, identifying potential vulnerabilities related to unauthorized access or privileged accounts.
The Importance of NSA Maps in Network Security
Creating an NSA map is a fundamental step in establishing a robust network security posture. Its significance stems from several key benefits:
- Comprehensive Network Visibility: The map provides a holistic view of the entire network, allowing security professionals to identify potential blind spots and vulnerabilities that might otherwise go unnoticed.
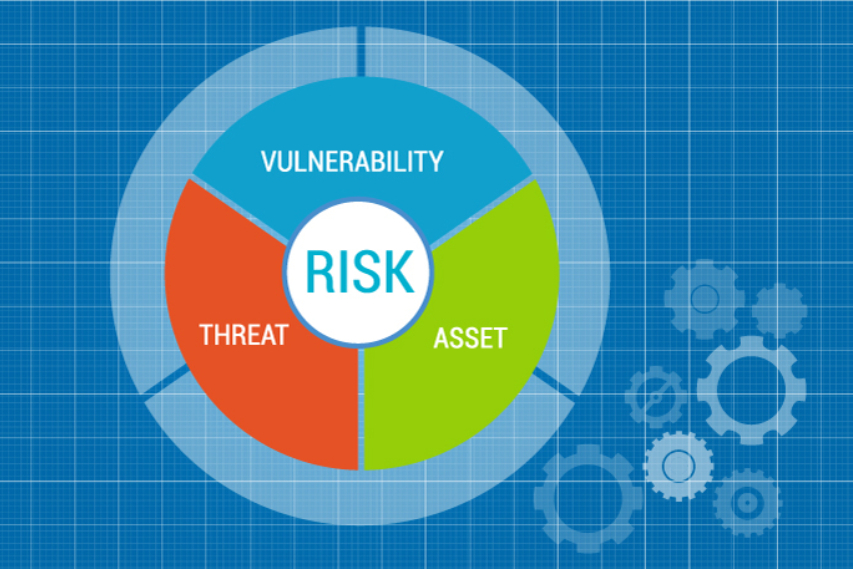
- Vulnerability Identification: By analyzing the map, security professionals can identify specific vulnerabilities based on device types, operating systems, software applications, and network configurations.
- Prioritized Security Efforts: The map helps prioritize security efforts by focusing on the most critical vulnerabilities and high-risk areas, ensuring efficient resource allocation.
- Risk Assessment and Mitigation: The map facilitates comprehensive risk assessment, enabling security professionals to evaluate potential threats and implement targeted mitigation strategies.
- Incident Response Planning: In the event of a security breach, the map provides valuable information for incident response teams, enabling them to quickly identify affected systems and implement containment measures.
- Compliance and Auditing: The map serves as a valuable tool for demonstrating compliance with industry standards and regulations, facilitating audits and assessments.
- Improved Communication: The map provides a common language for communication between security professionals, IT personnel, and management, ensuring everyone understands the network’s security posture.
Constructing an NSA Map: A Step-by-Step Guide
Creating an accurate and comprehensive NSA map requires a systematic approach:
- Network Discovery: Begin by conducting a thorough network discovery to identify all connected devices and systems. This can be achieved through network scanning tools, network management systems, or manual inventorying.
- Data Collection: Gather relevant security information about each device, including operating system, software applications, network connectivity, security measures, and user access. This can be obtained through configuration files, security logs, and interviews with relevant personnel.
- Map Creation: Utilize specialized mapping software or diagramming tools to create a visual representation of the network infrastructure. This map should clearly depict the connections between devices, highlighting critical security information.
- Verification and Validation: Regularly review and update the map to ensure its accuracy and reflect any changes in the network infrastructure. This process involves verifying the information collected and validating the map against actual network configurations.
- Continuous Monitoring: Implement continuous monitoring of the network infrastructure to detect changes and update the map accordingly. This ensures that the map remains relevant and reflects the current security posture.
FAQs Regarding NSA Maps
1. What are the common tools used for creating NSA maps?
Several tools are available for creating NSA maps, including:
- Network Mapping Software: Specialized software like SolarWinds Network Performance Monitor, ManageEngine OpManager, and Auvik provide comprehensive network discovery and mapping capabilities.
- Diagramming Tools: General-purpose diagramming tools like Microsoft Visio, Lucidchart, and Draw.io can be used to create visual representations of network infrastructure.
- Network Management Systems (NMS): NMS like Cisco Prime Infrastructure and HP OpenView provide network management and visualization capabilities, including network mapping.
- Security Information and Event Management (SIEM) Systems: SIEM systems like Splunk and IBM QRadar can be used to collect and analyze security data, providing insights for network mapping.
2. How often should an NSA map be updated?
The frequency of updates depends on the organization’s network dynamics and security posture. However, it is generally recommended to update the map:
- Regularly: At least quarterly or semi-annually to reflect changes in network configuration, software updates, and security measures.
- After Significant Changes: After major network infrastructure changes, such as new device installations, software upgrades, or network reconfiguration.
- Following Security Incidents: After security incidents to identify affected systems and implement mitigation measures.
3. What are the common challenges in creating and maintaining NSA maps?
Creating and maintaining accurate and comprehensive NSA maps can be challenging due to:
- Network Complexity: Large and complex networks with numerous devices and connections can be difficult to map effectively.
- Data Availability: Gathering complete and accurate security information about all network components can be challenging due to data silos and inconsistent documentation.
- Dynamic Network Changes: Networks are constantly evolving, making it difficult to keep the map up-to-date with changes in configuration, device additions, and software updates.
- Resource Constraints: Allocating sufficient resources, including time and personnel, for map creation and maintenance can be a challenge for organizations with limited budgets and staff.
Tips for Effective NSA Map Creation and Maintenance
- Establish a Clear Process: Define a clear process for creating and maintaining the map, including roles and responsibilities, data collection methods, and update frequency.
- Utilize Automated Tools: Leverage network mapping software and other automated tools to streamline the process of network discovery, data collection, and map creation.
- Integrate with Security Tools: Integrate the NSA map with other security tools, such as vulnerability scanners and intrusion detection systems, to enhance security assessments.
- Collaborate with IT Teams: Foster collaboration between security and IT teams to ensure the map accurately reflects the network infrastructure and security configuration.
- Regularly Review and Update: Establish a regular review and update schedule to ensure the map remains accurate and reflects the current network security posture.
Conclusion
An NSA map is an indispensable tool for navigating the complex world of network security. By providing a comprehensive understanding of an organization’s network infrastructure, identifying potential vulnerabilities, and guiding mitigation strategies, NSA maps empower security professionals to proactively protect their networks from cyber threats. Embracing the benefits of NSA maps is crucial for organizations seeking to establish a robust and resilient network security posture, ensuring the confidentiality, integrity, and availability of critical data and systems.
![What is a Network Security Assessment? [+How to Conduct & Best Tools]](https://gogetsecure.com/wp-content/uploads/2022/03/What-is-Network-Security-Assessment-1024x512.jpg)


![What is a Network Security Assessment? [+How to Conduct & Best Tools]](https://gogetsecure.com/wp-content/uploads/2022/03/Network-Security-Assessment.jpg)

Closure
Thus, we hope this article has provided valuable insights into Navigating the Network: A Comprehensive Guide to Network Security Assessments (NSA) Maps. We appreciate your attention to our article. See you in our next article!
